
dHEDGE
dHEDGE is a one-stop location for managing investment activities on the blockchain where you can put your capital to work in different strategies based on a transparent track record. Multi-chain, non-custodial, decentralized asset management integrated with multiple protocols; allowing for trades, providing liquidity and yield farming.
PoC Required
Rewards
Rewards by Threat Level
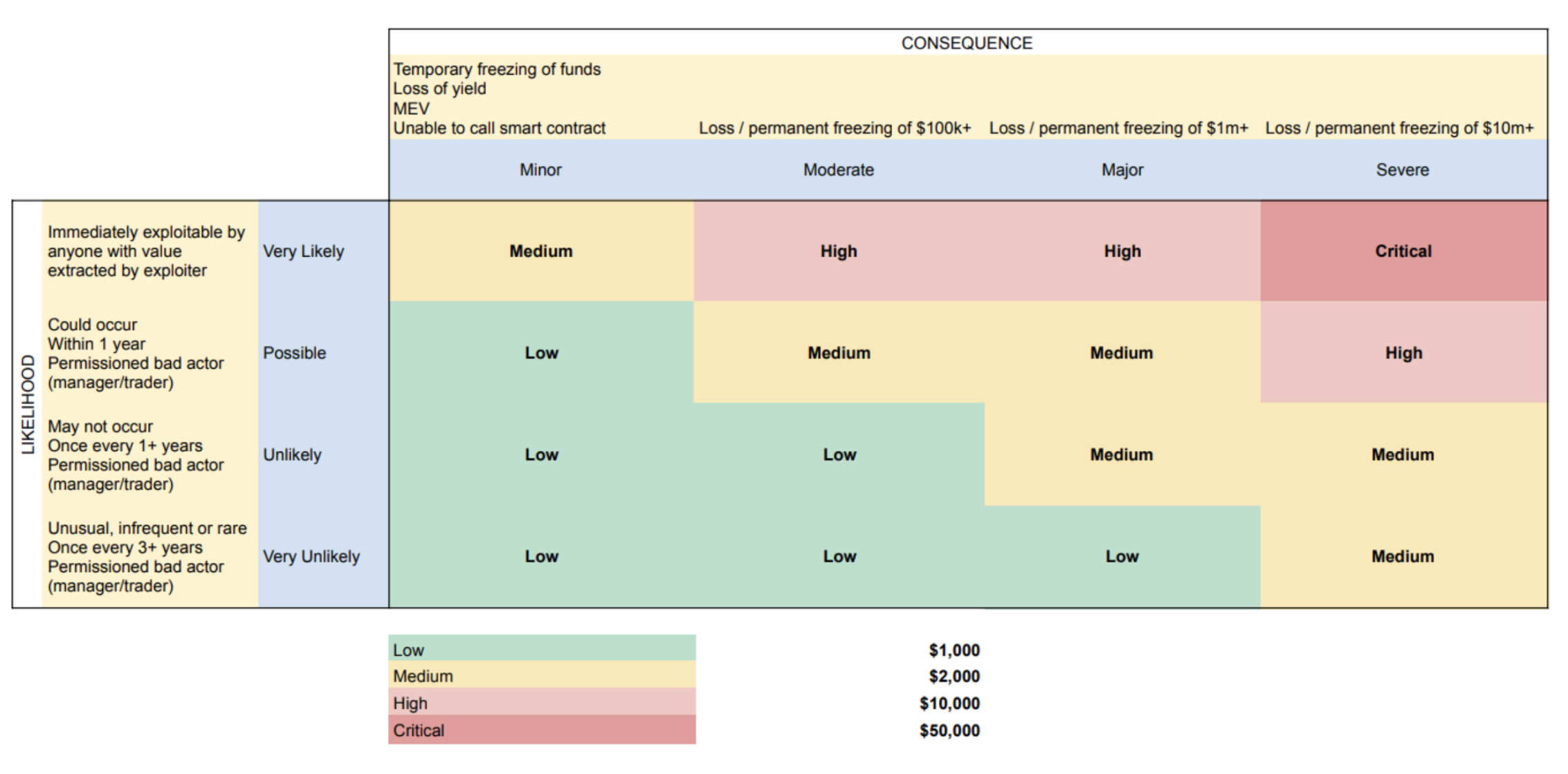
Rewards are distributed according to the impact of the vulnerability based on the Immunefi Vulnerability Severity Classification System V2.2. This is a simplified 5-level scale, with separate scales for websites/apps and smart contracts/blockchains, encompassing everything from consequence of exploitation to privilege required to likelihood of a successful exploit.
There is one exception for this bug bounty program, which overrides one vulnerability in the vulnerability scale, in the above Immunefi Vulnerability Severity Classification System:
- The vulnerability of: “Token holders temporarily unable to transfer holdings” will be classified under this bug bounty program as a medium vulnerability.
Vulnerabilities marked as “Acknowledged” in the https://www.certik.org/projects/dhedge are not eligible for a reward.
dHedge vaults are trust minimized, meaning that the vault manager may not follow a set strategy, or may make bad trades, including trades with poor slippage. A complete loss of funds is possible via poor risk-management strategies by the manager. These types of losses are not in scope for the bounty.
Payouts are handled by the dHEDGE team directly and are denominated in USD. However, payouts are done in USDC.
Please note, from May, 22nd through June 17th, dHEDGE will be undergoing a Public Audit. During this time, any in-scope bug submission reported to this program, that was also submitted for the contest, by one or more reporters, will be considered a 'Known Issue' and closed as out of scope. Additionally, valid bug reports submitted during the audit may have their rewards delayed until the audit is completed.A full list of reported known issues will be provided, and this program will be updated once the audit is completed.
Program Overview
dHEDGE is a one-stop location for managing investment activities on the blockchain where you can put your capital to work in different strategies based on a transparent track record. Multi-chain, non-custodial, decentralized asset management integrated with multiple protocols; allowing for trades, providing liquidity and yield farming.
For more information about dHEDGE, please visit https://app.dhedge.org/.
This bug bounty program is focused on their smart contracts and is focused on preventing:
- Loss of user funds by freezing or theft
- Loss of governance funds
- Theft of unclaimed yield
- Freezing of unclaimed yield
- Temporary freezing of funds for any amount of time
- Deposit and withdrawal bugs
- Protocol integration bugs
KYC not required
No KYC information is required for payout processing.
Proof of Concept
Proof of concept is always required for all severities.
Prohibited Activities
- Any testing on mainnet or public testnet deployed code; all testing should be done on local-forks of either public testnet or mainnet
- Any testing with pricing oracles or third-party smart contracts
- Attempting phishing or other social engineering attacks against our employees and/or customers
- Any testing with third-party systems and applications (e.g. browser extensions) as well as websites (e.g. SSO providers, advertising networks)
- Any denial of service attacks that are executed against project assets
- Automated testing of services that generates significant amounts of traffic
- Public disclosure of an unpatched vulnerability in an embargoed bounty
- Any other actions prohibited by the Immunefi Rules
Feasibility Limitations
The project may be receiving reports that are valid (the bug and attack vector are real) and cite assets and impacts that are in scope, but there may be obstacles or barriers to executing the attack in the real world. In other words, there is a question about how feasible the attack really is. Conversely, there may also be mitigation measures that projects can take to prevent the impact of the bug, which are not feasible or would require unconventional action and hence, should not be used as reasons for downgrading a bug's severity.
Therefore, Immunefi has developed a set of feasibility limitation standards which by default states what security researchers, as well as projects, can or cannot cite when reviewing a bug report.

